Month
March 2017
While I was busy setting up my new router for my whole home VPN, I took advantage of that opportunity to make a few other changes to my network in order to make it more secure. In particular, I created a new WiFi network to be used exclusively by so called “Internet of Things” (IoT) devices in my home.
If you’ve been paying attention to tech news, you’ve probably seen reports of IoT devices being hacked en masse. Everything from thermostats, to lightbulbs, to electrical switches, to refrigerators have been reported as hacked and turned against their intended purpose. Results have reportedly included a refrigerator that is used as a spam gateway, electrical switches that have been turned into a botnet for DDOS attacks, and lightbulbs that expose their owners WiFi passwords.
To put it mildly, IoT devices have a horrible security reputation and are generally regarded as some of the least secure devices likely to be attached to a home network. To make things worse, once one IoT device is compromised on your network, it often begins probing other network attached devices looking for weaknesses that it can exploit. That’s bad enough when those other devices are other lightbulbs, but it could be catastrophic if your desktop computer was compromised. In that case, sensitive personal information saved on your computer could be exposed, and your personal contact list could be used to further propagate malware to everyone you know.
Despite their horrible security, IoT devices are really handy. I like being able to check my thermostat while away, and have lamps automatically turn on at sunset. So if I’m not willing to get rid of the IoT things in my home, how can I at least mitigate the damage they can do? It turns out that there is one thing you can do that will dramatically improve the security of your home network – segregate IoT devices from other computers on your network.
Segregating your IoT devices doesn’t have to be something as complicated as creating a separate subnet and messing with routing tables. In fact most modern routers have tools built-in to segregate untrusted network devices onto their own “guest network.” So what I did was create a separate guest WiFi network for the exclusive use of IoT devices. Now if one of my devices gets hacked, at least they won’t be able to reach really important devices like my desktop computer and backup server. At worst, they will be able to infect other IoT devices on my network.
If you follow this advice on your own network, I suggest you enable “AP Isolation” mode on your guest network, if it is available. This mode restricts devices attached to the network from being able to talk to each other. Instead, they can only reach the Internet. This further protects devices on your network and prevents your lightbulb from hacking into your electrical switch, for example. (Lightbulbs hacking into electrical switches – What a world we live in!)
Posted on March 13, 2017
A few days ago, I was browsing Twitter (as I am wont to do) and came across a tweet from the ACLU publicizing their statement opposing a Senate resolution that would allow Internet service providers (ISP) to sell customer browsing data without the customer’s permission. Unsurprisingly, selling your browsing data is something that the big ISPs have been wanting to do for years. This proposal would give them that ability and more, since they wouldn’t even have to ask the customer’s permission. Instead, they could just comb their logs for browsing data, sell it to the highest bidder, and reap the profits. Easy money.
Now I’m not going to dive into the politics of all this. You may feel it’s perfectly OK for ISPs to engage in this sort of behavior, and that’s fine. I, however, am totally creeped out by the prospect. Although SSL/TLS (aka “HTTPS”) may keep the content of my browsing secure from the prying eyes of my ISP, they still know which websites I visit – they have to in order to route my packets to their destination – and they can learn a lot from just that information. My ISP knows about that vacation I’m planning from my research of area attractions. (I’m sure airlines, car rental companies, and hotels would love that information so they could target me with ads.) My ISP learns about that unfortunate medical diagnosis from the sudden uptick in visits to medical websites like WebMD. (I bet my insurer and potential employers would be interested in that.) They can even tell my political leanings from the candidates I research and news outlets I frequent. (Truly dangerous information in some parts of the world.) So, long story short, I realized that although I may not be able to keep my ISP from tracking my packets, I can make that information worthless by using a virtual private network (VPN).
A VPN acts as an encrypted data tunnel connecting me to a remote server. I basically become part of the VPN provider’s network. Of particular interest to me, a VPN effectively hides the destination of internet traffic travelling over it from intermediaries. In other words, my ISP knows that there is traffic leaving my home, but it can’t see where it is going. All it can know is that the data is going to my VPN provider, and from there it doesn’t know to where the packets are routed. And since VPN traffic is (almost always) encrypted, a VPN also prevents my ISP from examining the content of my traffic – even traffic that isn’t protected by SSL/TLS.
So I knew that I wanted a VPN service, but I also knew that I didn’t want it to be a hassle. I didn’t want to have to log in, or flip a switch or do anything else every time I wanted to jump on the web, because I knew I wouldn’t do it due to the inconvenience. And as I discovered, the best way to do that was in the router. Now lots of modern routers will act as a VPN server, allowing you to create a VPN from the coffee shop you’re sitting in to your home in order to protect your web browsing from the untrustworthy barrista that just served you. Significantly fewer routers will act as a VPN client, routing outbound traffic to another VPN server. The distinction may seem minor, but it’s significant. I needed a router that has a VPN client mode.
The decision to use the router as a VPN client also imposed some other requirements upon me. As I mentioned above, VPN connections are typically encrypted, and although the overhead attached to encrypting and decrypting traffic isn’t too taxing for the CPU of a desktop or even mobile device, routers typically have CPUs that pale in comparison. So I needed a router with a (relatively) beefy CPU and plenty of of RAM.
After some research, what I settled on is the RT-AC88U router from Asus. It’s got 802.11ac wifi, gigabit ethernet, and is universally praised in reviews for its excellent wireless range. (It’s also ugly as sin, but we can’t have everything.) Of particular importance to my application, it has a fast dual-core CPU (by router standards) and double the RAM of many other models. Both of which help it stand up to the task of encrypting and decrypting a house-full of Internet traffic. The RT-AC88U also has a VPN client mode built into its firmware, which is a plus since I didn’t really want to have to flash it with custom firmware like DD-WRT. (DD-WRT is great, but I’m at a point in my life where I like my technology to just work without all the fiddling.)
So – step 1 – I bought an RT-AC88U and set it up like a regular router. I got the wifi set up, I mapped the few static IP addresses that I needed, and generally got my network back to a working state (without worrying about the VPN for the moment). The only big surprise at this step was how awesome this router is with wifi coverage. It completely puts the 5th generation Airport Extreme that it replaced to shame. Seriously, I can’t emphasize enough what a difference this made to areas of my home that previously had borderline signal quality. I am totally impressed by this Asus router.
If step 2 of my plan was getting the router set up as a VPN client, then step 2a was to select a VPN service, because it does no good to have a VPN client if you have nothing to connect it to. I did some more research, I read reviews from The Wirecutter, PC Magazine, Ars Technica, and more. The only consensus I could find for the best VPN service, is that there is no consensus on the best VPN service. I ended up going with Private Internet Access (which I will from here on refer to as “PIA” because their name is annoying) because it was recommended to me, it generally receives pretty good reviews online, and because it covered all the features I was most interested in, namely reasonable cost, speed, provided protocols (specifically OpenVPN), and a “no logging” policy for traffic crossing its network. (Permitting peer-to-peer file sharing and geo-masking wasn’t really an issue for me since I don’t download torrents and I don’t need to trick Netflix into thinking I live somewhere else. They might be issues for you, though.)
Once I had subscribed to PIA, it was time to actually set up the router to use the service. And this is where it all went pear shaped. You see, despite thoroughly researching routers, and thoroughly researching VPN services, I had failed to do any research at all on combinations of routers and VPN services. Turns out that was a mistake and it cost me lots of time. As I learned, most VPN services are geared towards consumers that want to connect their laptop to a VPN while they are at a coffee shop. Most VPN services have easy-to-use software for both desktop and mobile operating systems that makes it a breeze to connect a single machine to their VPN. But a router is most definitely not a general purpose computer. The software that makes it easy to connect your laptop to a particular VPN service won’t do you any good at all when it comes time to connect your router. In fact, many VPN services don’t bother documenting or supporting router connections to their service. Of those that do, most (including PIA) only support the most common third-party firmware like DD-WRT and sometimes Tomato. In particular, very few VPN services support connecting from routers running the stock Asus firmware that came loaded on my RT-AC88U, even though it was capable of such a connection. (A notable exception that was brought to my attention after the fact: Express VPN which offers setup tutorials for a number different stock router firmware.)
After much searching, I found very little information about setting up stock Asus firmware with PIA. In fact I found so little that I was resigned to installing DD-WRT. So then I started researching how to use the DD-WRT firmware with my RT-AC88U and found that recent builds of DD-WRT were having various stability problems on the RT-AC88U. Since an unstable router sounds like just about the most frustrating thing I can think of, I kept looking, and discovered Merlin.
The Asuswrt-Merlin project (which I will from here on refer to as simply “Merlin” because “Assuwrt-Merlin” is quite a mouthful, and because “Merlin” is a much cooler name) is an enhanced version of the stock Asus router firmware. Based on Asus’ opensource code, and enhanced with bugfixes and other minor features, Merlin strikes a very nice middle ground between the ease of use of the stock Asus firmware and the complexity (and flexibility) available in custom firmware like DD-WRT. Consider it Microsoft PowerToys for Asus routers.
Merlin is very easy to install. I just downloaded the most recent build for the RT-AC88U from the Merlin download page, verified the file’s SHA256 signature, and uploaded it through the router’s administration panel. About three minutes later, my router rebooted with the new, enhanced firmware.
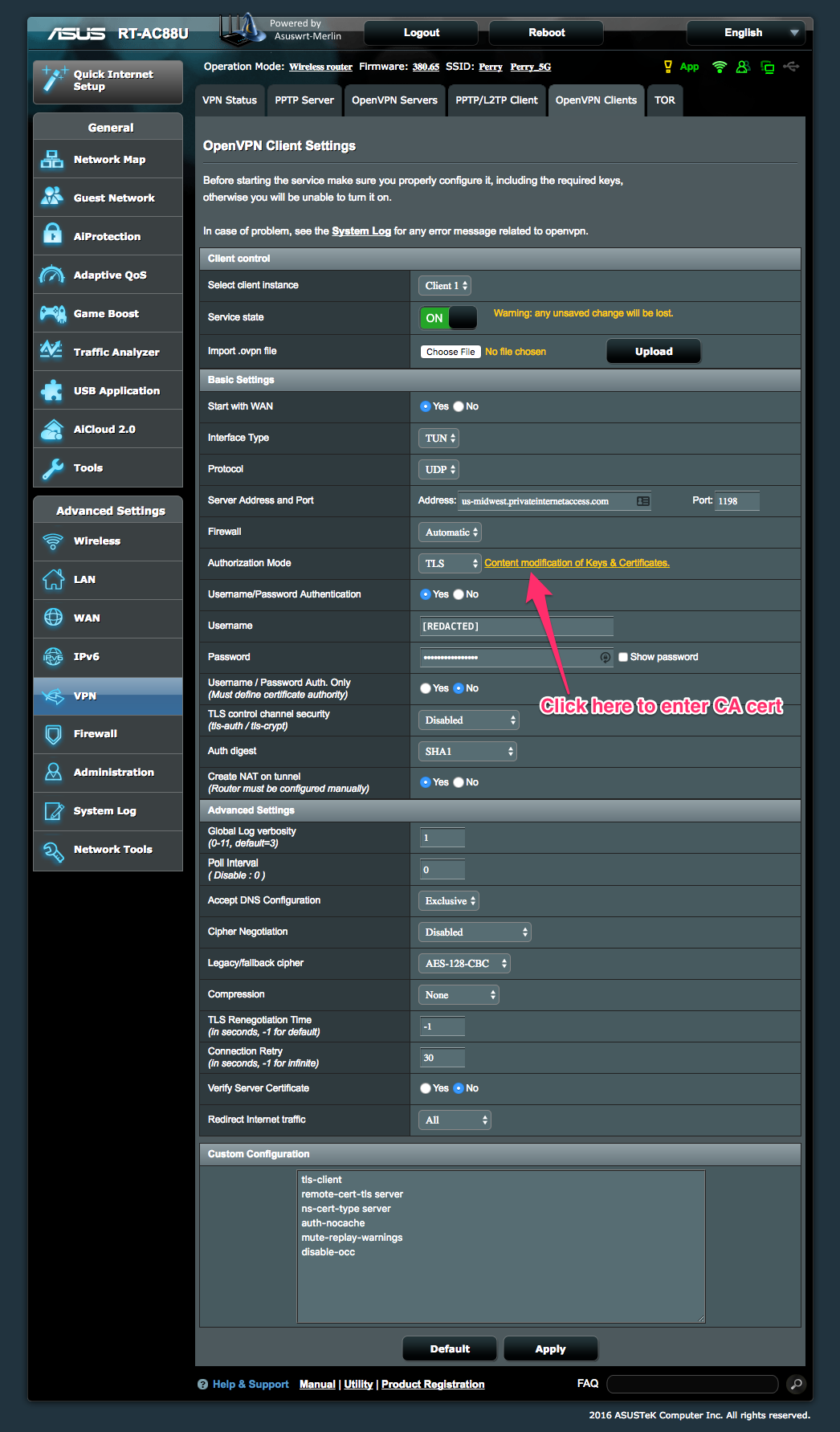
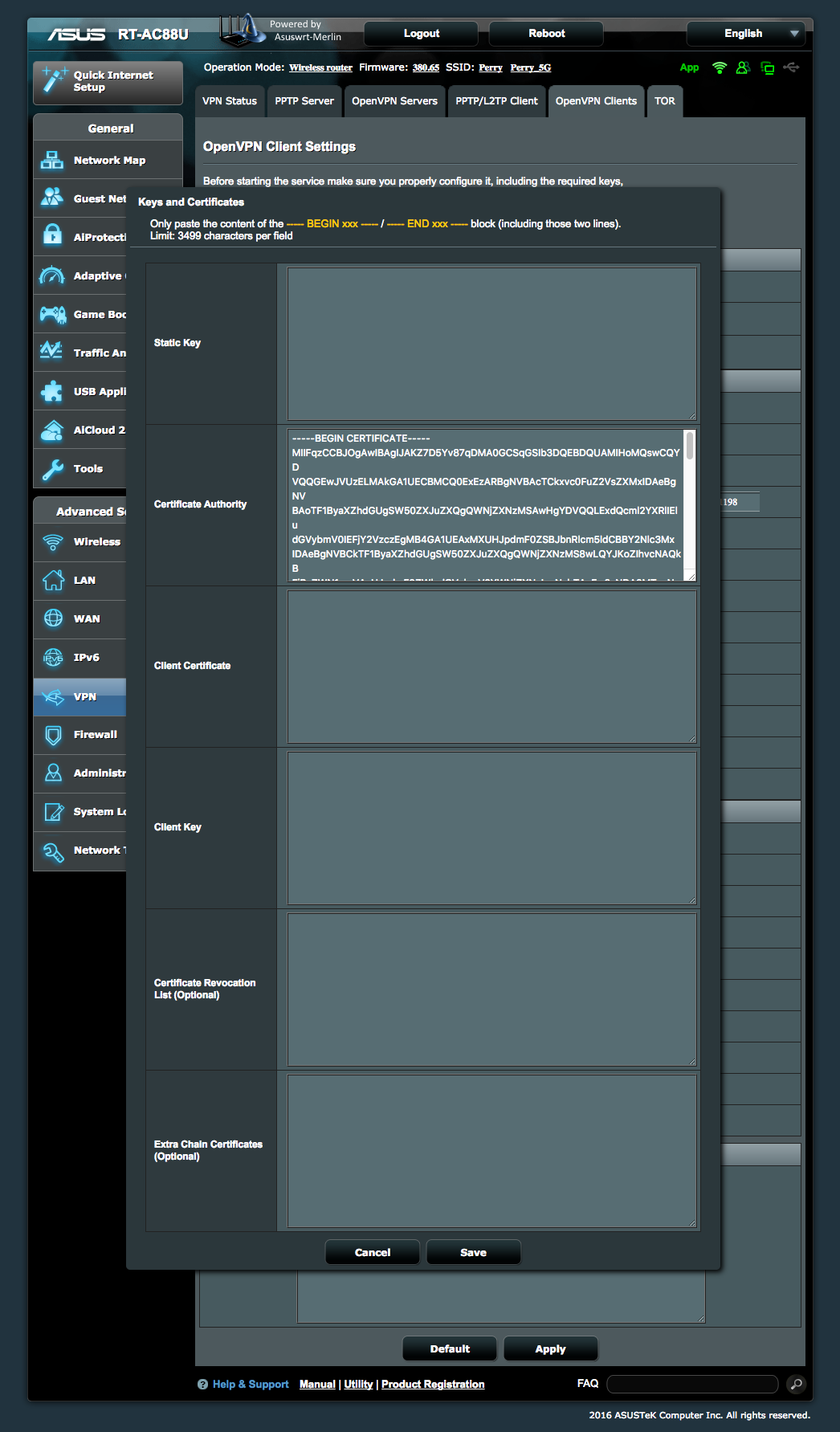
As for configuring the router’s VPN for PIA, I found very little help. PIA has an explicitly unsupported help document that’s a few versions out of date. I also found a helpful thread on SNBForums that appears to be periodically updated, but was still out of date as of this writing. For the benefit of those that find this post through the magic of Google, I am including below a screenshot of the final settings that got Merlin (Asuswrt-Merlin version 380.65) working with PIA. Note that after setting all options on main page, you need to click the “Content modification of Keys & Certificates” link (in the Authorization Mode row) to enter PIA Certificate Authority cert that you can download directly from PIA.
After configuring and enabling the VPN, I appeared to the various IP address geolocation services online as coming from somewhere in Kansas, rather than my own home in Indiana. They also report my ISP as Choopa, LLC rather than Comcast. So mission accomplished.
You might wonder how installing the VPS affected my Internet speed. I wondered too, so I did a little comparison. Without the VPN enabled, I get 89 Mbps down and 12 Mbps up. With the VPS enabled, I get 48 Mbps down and 11 Mbps up. (All speed scores are from Ookla Speedtest.) Most of that loss in speed I attribute to the overhead of my router handling the VPN encryption, however I have no data to back that up. In practice, I find that the speed hit is not noticeable in everyday web browsing, so I find it a small price to pay for privacy. (Although I may eat those words next time I have to download a large Xcode beta.)
So that’s it. I hope that others out there find this helpful. If you end up using this post to connect your own router to a VPN, I’d love to hear about it.